Whether you are living in a developed economy or a developing economy, one thing that is common is the rising number of use cases enabled leveraging the growing digital infrastructure. As digital adoption grows at a massive pace, malicious actors are also on the lookout to harness the possibility of exploiting the possible vulnerabilities in the products.
As per reports, cybersecurity threats like ransomware attacks, cryptojacking, cyber physical attacks, and other forms of online attacks are on a continuous rise (Source). Cyberattack of any form results in financial losses and irreparable damage to the brand. As there is so much at stake, businesses invest heavily in building a more secure, scalable, and reliable product.
Data must be secured whether it is in motion or at rest. This is where exhaustive Penetration testing can be extremely helpful since it helps in identifying the potential vulnerabilities in the product. Network penetration testing is a major testing approach that must be a part of vulnerability assessment. It is an integral part of the cyber security strategy, since it helps in validating security related aspects of the product (i.e. website or app).
In this blog, we deep dive into the nitty gritty of network penetration testing. By the end of this blog, you would be in a position to build a network pen testing strategy that will be useful in simulating cyber attacks through different types of hacking techniques.
So, let’s get started…
What is Network Penetration Testing?
For starters, penetration testing is a testing methodology where cyber attacks are simulated on systems for identifying vulnerabilities in the system. It helps in identifying and later fixing the security loopholes before they are exploited by the malicious actors.
Network penetration testing is a form of penetration testing where the hacking techniques are used for strengthening the networks. Since a real-life attack is simulated, it provides an opportunity to the development and DevSecOps teams to fix the lingering security issues in the product.
An experienced penetration testing company can be an ideal partner to run network pen tests at scale. Such a partnership is useful in scenarios where the internal team does not have experience in devising and running network penetration tests.
In the subsequent sections of the blog, we would look into the benefits, tools, and other aspects related to network penetration testing.
Benefits of Network Penetration Testing
Before we look at the advantages, you need to ask one important question “Can we release a web product even if there are issues on the security front?”. Well, the short & simple answer to this question is “You should not!”
Having said that, here are some of the salient benefits of network pen tests:
- Strengthen the product and network security by taking actions before the secure issues (or loopholes) are exploited by hackers
- Develop team’s domain competency in the security domain as they get an opportunity to patch security problems in the product
- Prevent financial and brand damages that can happen due to cyber attacks
The next question is whether network penetration testing is optional or not? With the growing adoption of cloud, microservices, and other distributed technologies; it has become essential to ensure that data is secure at every moment.
This is possible by using the right network penetration tools for identifying security loopholes and strengthening the network to nullify any probability of cyberattacks.
Also Read: 5 Reasons Why Penetration Testing Is Important
Steps Of Network Penetration Testing
Here are some of the major steps that can help you in crafting a scalable network penetration testing strategy:
1. Information Gathering
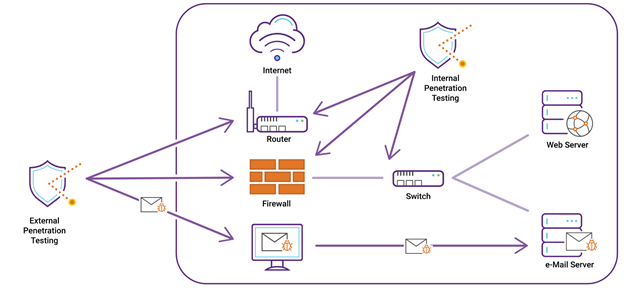
There are three main types of network penetration tests – Black box test, white box test, and gray box test. Black box network penetration testing comprises of a series of tests that are devised with limited knowledge of the internal network. It is the fastest and easiest way to detect security issues in the system.
The major downside is that the tests might not be sufficient to unearth major security loopholes in the product. Gray box network penetration testing comprises of tests that are devised from an end user’s perspective. The privileges are elevated so that the tester has access to every aspect of the system. Gray box testing is instrumental in unearthing internal as well as external vulnerabilities of the system.
White box network penetration testing comprises of a series of tests that are devised and executed from the perspective of IT & IS users. This form of testing is most beneficial for identifying security issues since users have access to the architecture and documentation. It scrutinizes the network and identifies almost every vulnerability in the system.
You should choose the type of penetration testing that is suited to the project requirements. You can involve technical as well as non-technical personnel when using black box network penetration testing since that approach requires minimal (to no) understanding of the internals of the product.
2. Reconnaissance And Discovery
It’s time for some action 🙂 Port and network scanners are used in the reconnaissance phase to detect vulnerabilities in the network and systems. This information will be helpful in searching for attack points like open ports, unpatched software, and more.
3. Running Network Penetration Tests
With the vulnerabilities identified in the earlier step, it’s time to run the network penetration tests. You can make use of tools like NMap, WireShark, etc. with custom-made scripts or default scripts to exploit the vulnerabilities.
Along with the technical approach where tools are used, you should also try phishing attacks for checking if the data that is internal to the company (e.g. employee information, vendor information, etc.) is safe or not.
4. Reporting and Remediation
Now that the vulnerabilities are identified from the earlier steps, the next step is to document every aspect of the vulnerabilities. The detailed report must include the vulnerability type, severity, priority, and more.
All the identified vulnerabilities pose different levels of risk to the business, which is why the reporting & analysis phase must be followed with remediation. Security patches and updates must be pushed by the security and/or DevSecOps teams.
Post the update, the entire testing cycle has to be repeated before the identified issues can be brought to closure.
Also Read: A Complete Guide to the Stages of Penetration Testing
Conclusion
Network penetration testing is no longer an option since every business uses some kind of cloud infrastructure for their product. A company specialized in providing penetration testing services can play a huge role in accelerating the network pen testing process.
Investing in strengthening the security aspects goes a long way in building a positive brand – a factor that will be helpful in scaling the product at a much faster pace!